nginx1.10.2添加modsecurity
ModSecurity 简介
ModSecurity是一个入侵侦测与防护引擎,它主要是用于Web 应用程序,所以也被称为Web应用程序防火墙。
它可以作为Apache Web服务器的模块或是单独的应用程序来运作。
ModSecurity的功能是增强Web application的安全性和保护Web application以避免遭受来自已知与未知的攻击。
听说与nginx配合,效果也很好。
环境:
CentOS Linux release 7.7.1908 (Core)
nginx/1.10.2
modsecurity-v3.0.3
ModSecurity-nginx-master
owasp-modsecurity-crs-3.0-master1、编译nginx
./configure --prefix=/usr/local/nginx --with-openssl=/root/openssl-1.0.2l/ --with-http_ssl_module2、安装nginx报错:
/root/nginx-sticky-module-1.1/ngx_http_sticky_module.c
/root/nginx-sticky-module-1.1/ngx_http_sticky_module.c: 在函数‘ngx_http_get_sticky_peer’中:
/root/nginx-sticky-module-1.1/ngx_http_sticky_module.c:333:21: 错误:赋值时将整数赋给指针,未作类型转换 [-Werror]
iphp->rrp.current = iphp->selected_peer;
^
cc1: all warnings being treated as errors
make[1]: *** [objs/addon/nginx-sticky-module-1.1/ngx_http_sticky_module.o] 错误 1
make[1]: 离开目录“/root/nginx-1.10.2”
make: *** [build] 错误 23、修改文件ngx_http_sticky_module.c (主要是#if到#endif这块)
if (peer && selected_peer >= 0) {
ngx_log_debug(NGX_LOG_DEBUG_HTTP, pc->log, 0, "[sticky/get_sticky_peer] peer found at index %i", selected_pe
er);
#if defined(nginx_version) && nginx_version >= 1009000
iphp->rrp.current = peer;
#else
iphp->rrp.current = iphp->selected_peer;
#endif
pc->cached = 0;
pc->connection = NULL;
pc->sockaddr = peer->sockaddr;
pc->socklen = peer->socklen;
pc->name = &peer->name;4、再次安装nginx,安装成功。
5、建立modsecurity的动态链接
./configure --prefix=/usr/local/nginx --with-openssl=/root/openssl-1.0.2l/ --with-http_ssl_module --add-module=/root/nginx-sticky-module-1.1 --add-dynamic-module=/root/ModSecurity-nginx-master
make && make install
mkdir /usr/local/nginx/modules
cp /root/nginx-1.10.2/objs/ngx_http_modsecurity_module.so /usr/local/nginx/modules/6、配置modsecurity
[root@nessus nginx]# mkdir /usr/local/nginx/modsec
[root@nessus nginx]# cp ~/modsecurity-v3.0.3/modsecurity.conf-recommended /usr/local/nginx/modsec/modsecurity.conf
[root@nessus nginx]# sed -i 's/SecRuleEngine DetectionOnly/SecRuleEngine On/' /usr/local/nginx/modsec/modsecurity.conf7、手动创建main.conf文件
[root@nessus modsec]# cat /usr/local/nginx/modsec/main.conf
# From https://github.com/SpiderLabs/ModSecurity/blob/master/\
# modsecurity.conf-recommended
#
# Edit to set SecRuleEngine On
Include "/usr/local/nginx/modsec/modsecurity.conf"
# Basic test rule
SecRule ARGS:testparam "@contains test" "id:1234,deny,status:403"
[root@nessus modsec]# 8、nginx.conf首行添加
load_module modules/ngx_http_modsecurity_module.so; #添加modsecurity的模块9、在nginx.conf 在server块添加
server {
modsecurity on; #启用modsecurity
modsecurity_rules_file /usr/local/nginx/modsec/main.conf; #指定规则文件路径
listen 80;
server_name localhost;10、复制unicode.mapping到modsec
cp /root/modsecurity-v3.0.3/unicode.mapping /usr/local/nginx/modsec/不然会报错:
[root@nessus sbin]# ./nginx -t
nginx: [emerg] "modsecurity_rules_file" directive Rules error. File: /usr/local/nginx/modsec/modsecurity.conf. Line: 236. Column: 17. Failed to locate the unicode map file from: unicode.mapping Looking at: 'unicode.mapping', 'unicode.mapping', '/usr/local/nginx/modsec/unicode.mapping', '/usr/local/nginx/modsec/unicode.mapping'. in /usr/local/nginx/conf/nginx.conf:37
nginx: configuration file /usr/local/nginx/conf/nginx.conf test failed11、测试nginx
[root@nessus ~]# /usr/local/nginx/sbin/nginx -t
nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful
[root@nessus ~]#12、启动nginx
[root@nessus ~]# /usr/local/nginx/sbin/nginx
[root@nessus ~]# ps -ef | grep nginx
root 25104 1 0 11:20 ? 00:00:00 nginx: master process /usr/local/nginx/sbin/nginx
nobody 25105 25104 0 11:20 ? 00:00:00 nginx: worker process
root 25107 21800 0 11:20 pts/0 00:00:00 grep --color=auto nginx
[root@nessus ~]# 13、测试拦截
[root@nessus ~]# curl localhost?testparam=test
<html>
<head><title>403 Forbidden</title></head>
<body bgcolor="white">
<center><h1>403 Forbidden</h1></center>
<hr><center>nginx/1.10.2</center>
</body>
</html>14、查看modsecurity日志:
[root@nessus ~]# cat /var/log/modsec_audit.log
---8xMZOadF---A--
[23/Oct/2019:11:22:01 +0800] 157180092113.733856 127.0.0.1 40190 127.0.0.1 80
---8xMZOadF---B--
GET /?testparam=test HTTP/1.1
User-Agent: curl/7.29.0
Host: localhost
Accept: */*
---8xMZOadF---D--
---8xMZOadF---E--
<html>\x0d\x0a<head><title>403 Forbidden</title></head>\x0d\x0a<body bgcolor="white">\x0d\x0a<center><h1>403 Forbidden</h1></center>\x0d\x0a<hr><center>nginx/1.10.2</center>\x0d\x0a</body>\x0d\x0a</html>\x0d\x0a
---8xMZOadF---F--
HTTP/1.1 403
Server: nginx/1.10.2
Date: Wed, 23 Oct 2019 03:22:01 GMT
Content-Length: 169
Content-Type: text/html
Connection: keep-alive
---8xMZOadF---H--
---8xMZOadF---I--
---8xMZOadF---J--
---8xMZOadF---Z--
[root@nessus ~]# OWASP ModSecurity核心规则集(CRS)
1、导入规则
上传owasp-modsecurity-crs-3.3-dev.zip
复制crs的配置文件
cp /root/owasp-modsecurity-crs-3.0-master/crs-setup.conf.example /usr/local/nginx/modsec/modsecurity_crs_10_setup.conf2、创建目录 用于存放规则
mkdir /usr/local/nginx/modsec/modsecurity-crs
cp /root/owasp-modsecurity-crs-3.0-master/rules/* /usr/local/nginx/modsec/modsecurity-crs/3、在/usr/local/nginx/modsecmain.conf末尾添加
Include modsecurity_crs_10_setup.conf
Include modsecurity-crs/REQUEST-901-INITIALIZATION.conf
Include modsecurity-crs/REQUEST-903.9001-DRUPAL-EXCLUSION-RULES.conf
Include modsecurity-crs/REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.conf
Include modsecurity-crs/REQUEST-905-COMMON-EXCEPTIONS.conf
#Include modsecurity-crs/REQUEST-910-IP-REPUTATION.conf #有点问题 先注释掉
Include modsecurity-crs/REQUEST-911-METHOD-ENFORCEMENT.conf
Include modsecurity-crs/REQUEST-912-DOS-PROTECTION.conf
Include modsecurity-crs/REQUEST-913-SCANNER-DETECTION.conf
Include modsecurity-crs/REQUEST-920-PROTOCOL-ENFORCEMENT.conf
Include modsecurity-crs/REQUEST-921-PROTOCOL-ATTACK.conf
Include modsecurity-crs/REQUEST-930-APPLICATION-ATTACK-LFI.conf
Include modsecurity-crs/REQUEST-931-APPLICATION-ATTACK-RFI.conf
Include modsecurity-crs/REQUEST-932-APPLICATION-ATTACK-RCE.conf
Include modsecurity-crs/REQUEST-933-APPLICATION-ATTACK-PHP.conf
Include modsecurity-crs/REQUEST-941-APPLICATION-ATTACK-XSS.conf
Include modsecurity-crs/REQUEST-942-APPLICATION-ATTACK-SQLI.conf
Include modsecurity-crs/REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf
Include modsecurity-crs/REQUEST-949-BLOCKING-EVALUATION.conf
Include modsecurity-crs/RESPONSE-950-DATA-LEAKAGES.conf
Include modsecurity-crs/RESPONSE-951-DATA-LEAKAGES-SQL.conf
Include modsecurity-crs/RESPONSE-952-DATA-LEAKAGES-JAVA.conf
Include modsecurity-crs/RESPONSE-953-DATA-LEAKAGES-PHP.conf
Include modsecurity-crs/RESPONSE-954-DATA-LEAKAGES-IIS.conf
Include modsecurity-crs/RESPONSE-959-BLOCKING-EVALUATION.conf
Include modsecurity-crs/RESPONSE-980-CORRELATION.conf4、规则文件名解释:
主要规则文件:
REQUEST-910-IP-REPUTATION.conf(可疑IP匹配)
REQUEST-912-DOS-PROTECTION.conf(DDOS攻击)
REQUEST-913-SCANNER-DETECTION.conf(扫描器检测)
REQUEST-920-PROTOCOL-ENFORCEMENT.conf(HTTP协议规范相关规则)
REQUEST-921-PROTOCOL-ATTACK.conf(协议攻击)
举例:HTTP Header Injection Attack、HTTP参数污染
REQUEST-930-APPLICATION-ATTACK-LFI.conf(应用攻击-路径遍历)
REQUEST-931-APPLICATION-ATTACK-RFI.conf(远程文件包含)
REQUEST-932-APPLICATION-ATTACK-RCE.conf(远程命令执行)
REQUEST-933-APPLICATION-ATTACK-PHP.conf(PHP注入攻击)
REQUEST-941-APPLICATION-ATTACK-XSS.conf(XSS)
REQUEST-942-APPLICATION-ATTACK-SQLI.conf(SQL注入)
REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf(会话固定)
REQUEST-949-BLOCKING-EVALUATION.conf()
RESPONSE-950-DATA-LEAKAGES.conf(信息泄露)
RESPONSE-951-DATA-LEAKAGES-SQL.conf(SQL信息泄露)
RESPONSE-952-DATA-LEAKAGES-JAVA.conf(JAVA源代码泄露)
RESPONSE-953-DATA-LEAKAGES-PHP.conf(PHP信息泄露)
RESPONSE-954-DATA-LEAKAGES-IIS.conf(IIS信息泄露)
————————————————
版权声明:本文为CSDN博主「crystal_da」的原创文章,遵循 CC 4.0 BY-SA 版权协议,转载请附上原文出处链接及本声明。
原文链接:https://blog.csdn.net/Sydney_d/article/details/81740534也可以参考:https://blog.slogra.com/doc/modsecurity_crs.html
5、重启nginx:
/usr/local/nginx/sbin/nginx -s reload测试:(假装sql注入)
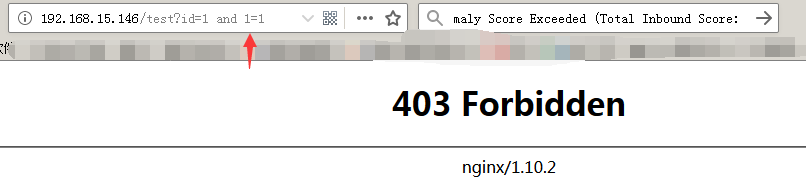
查看modsecurity后台日志:/var/log/modsec_audit.log
ModSecurity: Warning. Matched "Operator `Rx' with parameter `^[\d.:]+$' against variable `REQUEST_HEADERS:Host' (Value: `192.168.15.146' ) [file "/usr/local/nginx/modsec/modsecurity-crs/REQUEST-920-PROTOCOL-ENFORCEMENT.conf"] [line "777"] [id "920350"] [rev "2"] [msg "Host header is a numeric IP address"] [data "192.168.15.146"] [severity "4"] [ver "OWASP_CRS/3.0.0"] [maturity "9"] [accuracy "9"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-protocol"] [tag "OWASP_CRS/PROTOCOL_VIOLATION/IP_HOST"] [tag "WASCTC/WASC-21"] [tag "OWASP_TOP_10/A7"] [tag "PCI/6.5.10"] [hostname "192.168.10.126"] [uri "/test"] [unique_id "157181161484.259919"] [ref "o0,14v42,14"]
ModSecurity: Warning. detected SQLi using libinjection. [file "/usr/local/nginx/modsec/modsecurity-crs/REQUEST-942-APPLICATION-ATTACK-SQLI.conf"] [line "43"] [id "942100"] [rev "1"] [msg "SQL Injection Attack Detected via libinjection"] [data "Matched Data: 1&1 found within ARGS:id: 1 and 1=1"] [severity "2"] [ver "OWASP_CRS/3.0.0"] [maturity "1"] [accuracy "8"] [hostname "192.168.10.126"] [uri "/test"] [unique_id "157181161484.259919"] [ref "v13,9"]
ModSecurity: Access denied with code 403 (phase 2). Matched "Operator `Ge' with parameter `5' against variable `TX:ANOMALY_SCORE' (Value: `8' ) [file "/usr/local/nginx/modsec/modsecurity-crs/REQUEST-949-BLOCKING-EVALUATION.conf"] [line "44"] [id "949110"] [rev ""] [msg "Inbound Anomaly Score Exceeded (Total Score: 8)"] [data ""] [severity "2"] [ver ""] [maturity "0"] [accuracy "0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-generic"] [hostname "192.168.10.126"] [uri "/test"] [unique_id "157181161484.259919"] [ref ""]
ModSecurity: Warning. Matched "Operator `Ge' with parameter `5' against variable `TX:INBOUND_ANOMALY_SCORE' (Value: `8' ) [file "/usr/local/nginx/modsec/modsecurity-crs/RESPONSE-980-CORRELATION.conf"] [line "65"] [id "980130"] [rev ""] [msg "Inbound Anomaly Score Exceeded (Total Inbound Score: 8 - SQLI=5,XSS=0,RFI=0,LFI=0,RCE=0,PHPI=0,HTTP=0,SESS=0): SQL Injection Attack Detected via libinjection"] [data ""] [severity "0"] [ver ""] [maturity "0"] [accuracy "0"] [tag "event-correlation"] [hostname "192.168.10.126"] [uri "/test"] [unique_id "157181161484.259919"] [ref ""]实验完成
转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。
文章标题:nginx1.10.2添加modsecurity
本文作者:wangzhirui
发布时间:2019-11-12, 16:33:38
最后更新:2025-02-27, 02:04:06
原始链接:https://wangzhirui.com/2019/11/12/nginx1-10-2添加modsecurity/转载请保留原文链接及作者。